- Edge Browser Ios Download
- Edge Default Browser Ios
- Edge Browser Ios Review
- Edge Browser For Ios
- Microsoft Edge For Ios Review
Microsoft Edge is available to download on your iOS device. Easily sync your passwords, favorites, Collections, and other saved data across your signed-in devices. Microsoft has made apps for both iOS and macOS plenty of times in the past, but getting Microsoft's newest browser — Microsoft Edge — over to iOS has been a slow process. The iPhone has had Edge since November 2017; the iPad finally can get in on the fun!
A user agent (UA) string is able to be used to detect what version of a specific browser is being used on a certain operating system. Like other browsers, Microsoft Edge includes this information in the User-Agent HTTP header whenever it makes a request to a site. It may also be accessed via JavaScript by querying the value of navigator.userAgent.
Jugar tetris en calculadora casio. Microsoft recommends that web developers make use of feature detection whenever possible to improve code maintainability, reduce code fragility, and eliminate the risk of code breakage in the event of future UA string updates.
For cases where feature detection is not applicable and UA detection must be used, the format of the Microsoft Edge UA on desktop is as follows:
The User-Agent request header is in the following format:
The return value from navigator.userAgent is in the following format:
Platform identifiers change based on the operating system being used, and version numbers also increment as time passes. This format is the same as the Chromium UA with the addition of a new Edg token at the end. Microsoft selected the Edg token to avoid compatibility issues that may be caused by using the string Edge, which is used by the version of Microsoft Edge based on EdgeHTML. The Edg token is also consistent with existing tokens used on iOS and Android.
Mapping UA String to Browser Name
Mapping UA string tokens to a more human-readable browser name for use in code is a common pattern on the web today. When mapping the new Edg token to a browser name, Microsoft recommends using a different name than the one developers used for the legacy version of Microsoft Edge to avoid accidentally applying any legacy workarounds that are not applicable to Chromium-based browsers.
User Agent Overrides
Sometimes, a website does not recognize the updated version of the Microsoft Edge UA. As a result, a set of the features of that website may not work correctly. When Microsoft is notified about these types of issues, website owners are contacted and informed about the updated UA.
The sites often need some time to update and test the UA detection logic to address the issues that Microsoft reports to site owners. In these cases, Microsoft uses a list of UA overrides in our Beta and Stable channels to maximize compatibility for users who access these sites. The overrides specify new UA values that Microsoft Edge should send instead of the default UA for specific sites. You are able to view the list of UA overrides that are currently being applied by navigating to edge://compat/useragent in the Beta and Stable channels of Microsoft Edge.
Our Canary and Dev channels do not currently receive UA overrides so that web developers have an environment where they can easily reproduce issues on their sites that are caused by the default Microsoft Edge UA. If for some reason you require the ability to disable UA overrides in the Beta or Stable channels of Microsoft Edge, you may run the Microsoft Edge executable using the following command line argument:
Reading Time: 4minutesIt’s Time to Move to EDGE Mobile!
Back in November 2019 the Managed browser was announced to be retired March 31 2020. Already from February 1, 2020, the Intune Managed Application was going to removed from Google Play Store and iOS App Store. Since March is right around the corner, it’s about time to get prepared to do the switch.
Regarding a smooth transition, Microsoft let us use all the same Browser Config settings like “com.microsoft.intune.mam.managedbrowser”, so basically we just need to target the Edge for iOS and Android with the existing MAM Policies (app protection and app configuration settings).
With this blog post, I will cover the steps to get started and deep into the browser experience. And In my particular case, I’m going to use EDGE iOS as a corporate browser with some specific settings, just to show the user browser experience. We are also checking the custom settings like “Single sign-on”, Bookmarks and Blocking some specific sites from both end-user and MEM side.
Settings:
Step 1 ) App Protection Policies – Target Edge for iOS and Android
To get started we need to look into the existing App protection Policy.
Add EDGE to your Policy under Apps –> Edit and choose EDGE as a Public App (I’m Adding both iOS and Android).
Step 2) App configuration polices – Target Edge for iOS and Android
Change the App configuration polices for your particular configuration.
Add EDGE to your Policy under Basics –> Edit and choose EDGE as a Public App (I’m Adding both iOS and Android).
Edge Browser Ios Download
Step 3 ) Check out new Browser experience with EDGE
After adding the EDGE Application to the Policy, we can see that we now have a new layout. All settings have been merged to the “EDGE Configuration Settings” where the “com.microsoft.intune.mam.managedbrowser” is in the new view. You can see that is much easier to change settings without knowing all the “com.microsoft.intune.mam.managedbrowser” settings. We also have new settings like Import and Export either Blocked URLs which is a welcome addition.
Edge Default Browser Ios

Edge Browser Ios Review
In the video below you can see how the MAM policy is applied and how the browser experience looks when MAM configurations are applied.
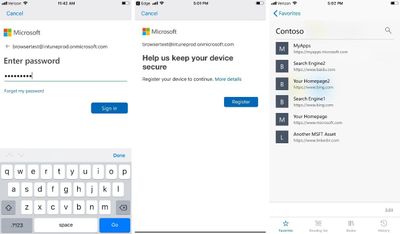
How does “Single sign-on” work on EDGE with iOS?
Edge Browser For Ios
I have not found any documentation regarding how the “Single Sign-on” Flow works. So to find how “SSO” was working with iOS, I had to dig into the EDGE browser logs. In the logs, I could find that EDGE is using Cross-app/ keychain sharing with Company Portal, and the SSO” flow is using ADAL – Azure AD v1.0 endpoint. So regarding the authorization flow, the Company Portal already has a valid Authorization Token, and the next request against Azure AD v1.0 endpoint will use the same Application ID. The EDGE Application has another redirect URI than the Company Portal application, but keychain sharing is part of the SDK, so it will use ADAL token. The figure below illustrates the Authentication Flow from 1 to 4. M730r mouse driver. I’m guessing this will change over time since Microsoft will probably migrate to using MSAL – Azure AD v2.0 endpoint eventually.
Summary
Microsoft Edge For Ios Review
The technical changes regarding adding EDGE as the new shiny browser is lucky for us not much work. The needed work will be to create new guides and information to the End-Users. During the pilot, I found one handy key feature when running both browsers for a period of time is that we can Direct users to Microsoft Edge instead of the Intune Managed Browser with custom settings.
In terms of new MAM Configuration settings, I hope that we will get some more control like changing the start page, so it automatically starts the browser like it did in the Managed Browser. I could also like that we have more control over the SSO settings so it Automatically starts the Sign-On view right after MAM Policy is applied.
Documentation:
